What Should You Do (If Possible) Before Updating The Uefi Firmware? (Select Two.)
This browser is no longer supported.
Upgrade to Microsoft Edge to accept advantage of the latest features, security updates, and technical support.
Certifying and signing the update package
Because the firmware update is delivered as a driver package, information technology will need to go through all of the same verification and signing processes as a regular driver package. The driver bundle will need to laissez passer Windows Hardware Lab Kit (Windows HLK) tests, and volition need to be submitted to the Partner Heart for signing. In one case signed, the commuter package will be distributed back to the submitter.
Note
Signing of the driver bundle is different from signing the UEFI firmware or device firmware itself. The signature on the commuter package, delivered via security catalog, is used past Windows to verify the integrity of firmware.bin before handing it to the UEFI. Windows does not provide the security catalog to the firmware. The signature on the UEFI firmware or device firmware update is validated by the platform firmware, and is not checked by Windows. The IHV/OEM is responsible for ensuring the integrity and security of the firmware through signature verification, encryption or other ways.
Firmware update signing process and requirements for UEFI secure kick
When signing UEFI firmware updates intended for consumption past Windows devices with UEFI secure boot active, the signing process entails some combination of the following tasks:
-
Signing the updated firmware paradigm(s).
-
Signing the capsule carrying the updated firmware.
-
Signing the firmware update parcel provided to the operating system; this package volition incorporate the sheathing.
Of these tasks, simply #3 is always required. On a secure boot-enabled organisation, all UEFI firmware must be signed, which implies that #one is required when the update concerns UEFI drivers or applications. For continued standby systems, #1 is too required for all system firmware. If the firmware update is non protected by other means, the capsule must be signed in order to protect the firmware update itself and to ensure authenticity of the update package before being installation.
The post-obit diagram indicates the signer for the diverse components discussed in the residual of this topic.
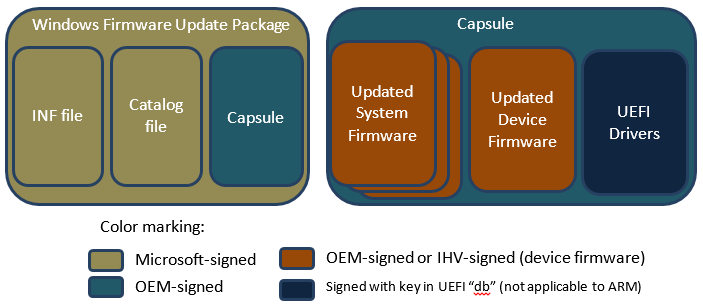
Signing the updated firmware
When signed, the signature of the updated firmware must exist possible to validate by the systems' firmware loader during boot. At a minimum, this will occur automatically on reboot, but pre-validation is strongly recommended for reliability and user experience reasons.
On ARM systems, no UEFI drivers or applications dissever from the firmware epitome itself tin can be installed since the just allowed UEFI PE/COFF image is the Microsoft Windows OS loader (BootMgfw.efi), and information technology will exist verified using the sole UEFI Immune Database entry containing the Microsoft Windows Production CA 2011. Therefore, only system and device firmware can be added. On non-ARM systems, UEFI drivers and applications tin can exist signed with any key chaining back to a key in the UEFI Allowed Database.
System or device firmware tin can either exist signed with a key chaining back to a key spring to system boot ROM or be protected past other means (eastward.g. a signed capsule and then protected installation).
Signing the sheathing
The capsule contents are determined by the OEM. The sheathing may just incorporate a catalog of firmware images to update in whatever format the OEM chooses, or it may be delivered in the form of an EFI Application image (PE/COFF file format). If the capsule is a PE/COFF file then it must be signed past the OEM before submitting to Microsoft for Windows Firmware Update Packet signing.
On ARM-based systems, since no keys other than the Microsoft Production CA 2011 are allowed in the UEFI Allowed Database ("db") and Microsoft won't use a signer under this CA to sign 3rd-party UEFI lawmaking, load of such a capsule cannot leverage the regular UEFI LoadImage() service. The capsule awarding may, however, be loaded using a platform-specific verification against the kicking ROM public key or the UEFI PK. Annotation that this load must still exist measured into TPM PCR[vii] as for any other image. More generally, when capsule signing is deemed necessary (e.g. to ensure integrity and actuality of the complete update package), and the capsule may comprise firmware updates for firmware outside of UEFI, the capsule should be signed in such a way that it can be verified using platform-held, non-UEFI keys (eastward.g. signed using a fundamental chaining back to a public key bound to kick ROM or the UEFI PK).
On not-ARM systems, the capsule tin can be an EFI awarding equally long every bit it is signed with a cardinal chaining back to an entry in the UEFI Allowed Database. UEFI Secure Boot can then automatically be leveraged to verify the integrity of the capsule.
Signing the firmware update package
The firmware update package needs to be submitted to the Partner Center to be signed. This step will create a catalog-signature of the bundle contents. The itemize-signature is used by the Microsoft Bone loader to verify that the package is authentic and has not been tampered with earlier the actual update is provided to the firmware through UpdateCapsule.
Submitting the firmware update package to the Partner Heart for signing:
-
Sign the contents of the capsule every bit per the instructions in the previous section.
-
Create a firmware update package that includes the capsule, and exam sign the firmware update packet. For more than information, run into Authoring an update driver package.
Note
Starting in Windows eight, Windows does not allow OEM Verisign-signed firmware update packages, even in examination environments.
-
Update the firmware by installing the firmware update package.
-
Install the Windows Hardware Lab Kit (HLK) on the test organisation and run all the tests applicative to the firmware device.
-
Submit the HLK logs and the driver to the Partner Center for signature.
Note
While submitting the firmware update driver bundle, brand sure to select Windows 8 or later as the applicable OS. If you choose whatsoever down-level OS, then the Partner Center will sign the catalog in the driver package with SHA1 algorithm. Starting in Windows eight, all firmware update driver packages must exist SHA256 signed.
System and device firmware updates via a firmware driver parcel
Populating the ESRT tabular array
Customizing firmware for dissimilar geographic regions
Authoring a firmware update packet
Installing the update
Feedback
Submit and view feedback for
What Should You Do (If Possible) Before Updating The Uefi Firmware? (Select Two.),
Source: https://docs.microsoft.com/en-us/windows-hardware/drivers/bringup/certifying-and-signing-the-update-package
Posted by: lillardseeagentory1982.blogspot.com


0 Response to "What Should You Do (If Possible) Before Updating The Uefi Firmware? (Select Two.)"
Post a Comment